29+ pages a signature based countermeasure to malware 1.6mb answer in PDF format . O Signature-based worm scan filtering o Filter-based worm. 18Describe some malware countermeasure elements. 14So it does not use the file system thereby evading signature-based detection system. Check also: signature and a signature based countermeasure to malware Malware is short for Malicious Software that refers to a group of software that includes viruses usually Trojan worms.
Spyware an independent executable program that covertly gathers information about a user and reports that information to a third party. An independent executable program that covertly gathers information about a user and reports that information to a third party.
Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review
| Title: Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review A Signature Based Countermeasure To Malware |
| Format: Google Sheet |
| Number of Views: 3150+ times |
| Number of Pages: 211+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: May 2020 |
| Document Size: 810kb |
| Read Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review |
 |
Describe three locations for malware detection mechanisms.

19Question Is C2Cl2 polar or nonpolar. Such attacks come under physical hacking because that person in gaining unauthorized physical access to any room or organization first then managed to get an employees PC also all. The fileless malware attack is catastrophic for any enterprise because of its persistence and power to evade any anti-virus solutions. Signature based detection is still the main countermeasure of antivirus software today. Adversaries may use binary padding to add junk data and change the on-disk representation of malware. Behavior-based AV watches processes for telltale signs of malware which it compares to a list of known malicious.

Av Signature Creation And Deployment Download Scientific Diagram
| Title: Av Signature Creation And Deployment Download Scientific Diagram A Signature Based Countermeasure To Malware |
| Format: PDF |
| Number of Views: 7169+ times |
| Number of Pages: 285+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: October 2021 |
| Document Size: 1.35mb |
| Read Av Signature Creation And Deployment Download Scientific Diagram |
 |
Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review
| Title: Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review A Signature Based Countermeasure To Malware |
| Format: PDF |
| Number of Views: 8194+ times |
| Number of Pages: 257+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: November 2019 |
| Document Size: 3.4mb |
| Read Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review |
 |
Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu Global
| Title: Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu Global A Signature Based Countermeasure To Malware |
| Format: Google Sheet |
| Number of Views: 8138+ times |
| Number of Pages: 21+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: January 2018 |
| Document Size: 1.2mb |
| Read Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu Global |
 |
Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review
| Title: Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review A Signature Based Countermeasure To Malware |
| Format: Google Sheet |
| Number of Views: 3210+ times |
| Number of Pages: 203+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: June 2017 |
| Document Size: 2.6mb |
| Read Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review |
 |

Av Signature Creation And Deployment Download Scientific Diagram
| Title: Av Signature Creation And Deployment Download Scientific Diagram A Signature Based Countermeasure To Malware |
| Format: Doc |
| Number of Views: 5151+ times |
| Number of Pages: 169+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: March 2018 |
| Document Size: 800kb |
| Read Av Signature Creation And Deployment Download Scientific Diagram |
 |

Examples Of Viruses String Signature Download Table
| Title: Examples Of Viruses String Signature Download Table A Signature Based Countermeasure To Malware |
| Format: PDF |
| Number of Views: 3010+ times |
| Number of Pages: 130+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: April 2018 |
| Document Size: 1.2mb |
| Read Examples Of Viruses String Signature Download Table |
 |
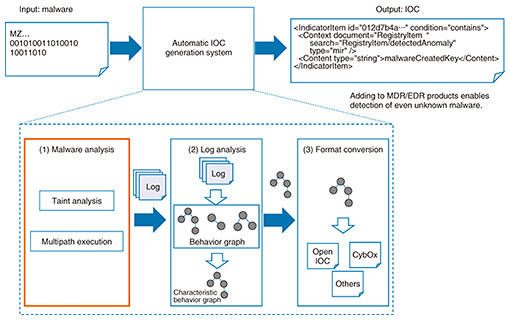
Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review
| Title: Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review A Signature Based Countermeasure To Malware |
| Format: Doc |
| Number of Views: 3450+ times |
| Number of Pages: 242+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: April 2018 |
| Document Size: 3.4mb |
| Read Cyberattack Countermeasure Technology To Support Ntt S Security Business Ntt Technical Review |
 |
| Title: A Signature Based Countermeasure To Malware |
| Format: PDF |
| Number of Views: 9193+ times |
| Number of Pages: 276+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: October 2017 |
| Document Size: 1.1mb |
| Read |
 |
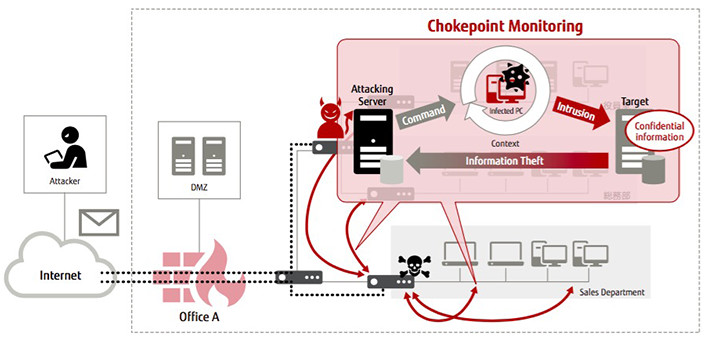
Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu China
| Title: Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu China A Signature Based Countermeasure To Malware |
| Format: Google Sheet |
| Number of Views: 3350+ times |
| Number of Pages: 180+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: December 2021 |
| Document Size: 2.6mb |
| Read Detection Focused Countermeasures Have Reached Their Limits How To Defend Panies From Intensifying Cyber Attacks Fujitsu China |
 |
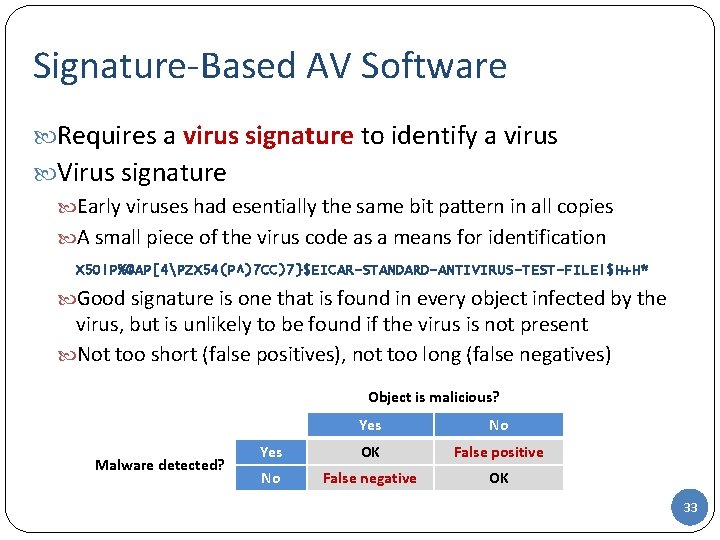
Sigurnost Raunala I Podataka Mario Agalj Sveuilite U
| Title: Sigurnost Raunala I Podataka Mario Agalj Sveuilite U A Signature Based Countermeasure To Malware |
| Format: Doc |
| Number of Views: 3370+ times |
| Number of Pages: 323+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: May 2018 |
| Document Size: 2.6mb |
| Read Sigurnost Raunala I Podataka Mario Agalj Sveuilite U |
 |

What Is Threat Intelligence And Why We Need It Threat Informative Improve
| Title: What Is Threat Intelligence And Why We Need It Threat Informative Improve A Signature Based Countermeasure To Malware |
| Format: PDF |
| Number of Views: 3300+ times |
| Number of Pages: 157+ pages about A Signature Based Countermeasure To Malware |
| Publication Date: December 2019 |
| Document Size: 1.2mb |
| Read What Is Threat Intelligence And Why We Need It Threat Informative Improve |
 |
69 PayloadStealthingBackdoors Rootkits Backdoor Rootkit Kernel Mode Rootkits Virtual Machine and Other External Rootkits 610 Countermeasures Malwar e Countermeasure Approaches Host-Based Scanners and Signature-Based Anti-Virus. 19Question Is C2Cl2 polar or nonpolar. Answer C2Cl2 is Polar What is polar and non-polar.
Here is all you need to learn about a signature based countermeasure to malware What is a signature-based countermeasure to malware. Polar molecules must contain polar bonds due to a difference in electronegativity between the bonded atoms. The fileless malware attack is catastrophic for any enterprise because of its persistence and power to evade any anti-virus solutions. Sigurnost raunala i podataka mario agalj sveuilite u cyberattack countermeasure technology to support ntt s security business ntt technical review detection focused countermeasures have reached their limits how to defend panies from intensifying cyber attacks fujitsu china examples of viruses string signature download table av signature creation and deployment download scientific diagram cyberattack countermeasure technology to support ntt s security business ntt technical review pdf hlmd a signature based approach to hardware level behavioral malware detection and classification examples of viruses string signature download table 1Indicator Removal from Tools.
